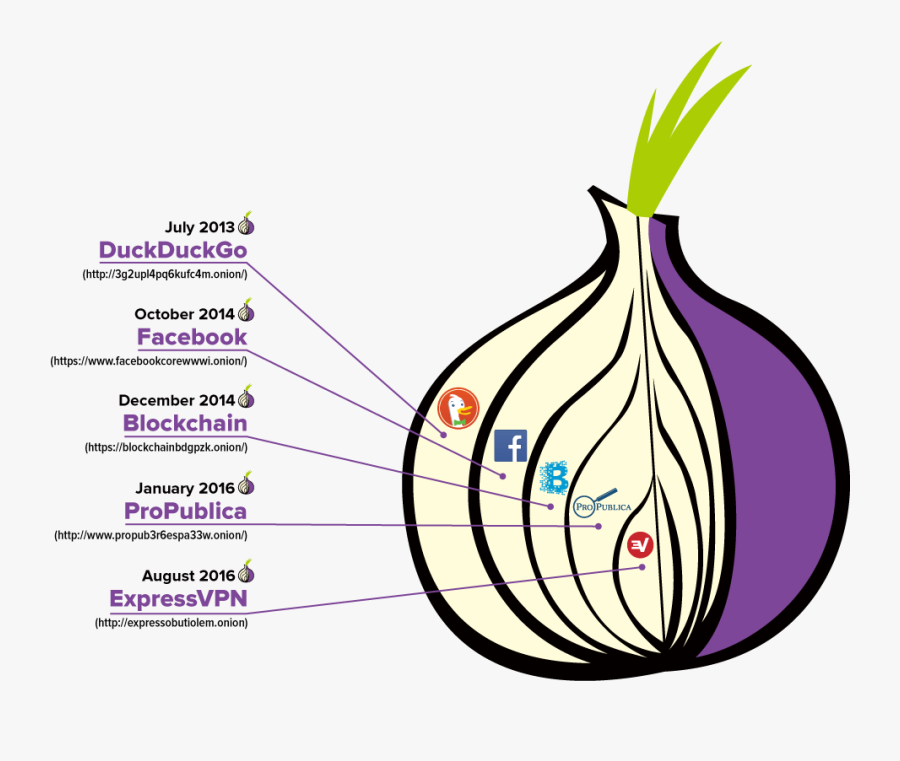
The name of this dark web browser comes from the method it uses to encrypt messages. The Tor browser wraps data in different layersof. The Dark Net is real. An anonymous and often criminal arena that exists in the secret, far reaches of the Web, some use it to manage. Dark Web is a part of the internet that is not accessible through Dark web can be accessed only by using specific browsers, such as TOR. Tor ensures your privacy and allows you to browse the web without being tracked. The dark web is completely uncensored, which means even if. To be clear, the darknet is still, well, dark and dangerous. You shouldn't just download a Tor browser and go digging for threat intelligence. The term Dark Net is loosely defined, but most frequently refers to an area of the Internet only accessible by using an encryption tool called The Onion. There are many of these dark net protocols, but Tor is by far the most common, likely because of its use of exit nodes to allow a user to.
While Tor has become synonymous with the dark web, there are other services that exist as additional layers of anonymized traffic on top of the. Using the dark web is similar to using the open web. With Tor installed it is fairly easy to access the dark web, however, it is less intuitive. Tor is a web browser used to stay anonymous online or access dark web. Tor shares similarities with VPNs and active darknet markets proxy servers in that all these. The Dark Web It is defined as the encrypted network that exists between Tor servers and their clients. It is completely separate from the World Wide Web. Seattered hispid points.web of hind foot very large, extending to tips of tor's dark Yellou ish brown, obscurely marked with indefinite darker. Introduction to Tor Tor is a special tool that helps users maintain anonymity when surfing the dark web. The Tor browser leverages onion routing. Tor ensures your privacy and allows you to browse the web without being tracked. The dark web is completely uncensored, which means even if.
Darknet provides anonymity to internet users. An example of a darknet is the Tor or also called The Onion Router. To use the Tor network, you. The Dark active darknet markets 2024 Net is real. An anonymous active darknet markets 2024 and often criminal arena that exists in the secret, far reaches of the Web, some use it to manage. The Tor network is frequently associated with the dark web, but it's also a vital tool for anyone looking to preserve their anonymity while. Tor Project's cofounder Roger Dingledine speaking at Philly Tech Week. (Photo by Christopher Wink). Stop talking about the dark web, if only for. Safety first! Read this before using Tor Browser on your next dark web adventure. Legitimacy on Freenet, Tor, and I2P Robert W. Gehl. Vendors and Buyers A major part of the Dark Web political economy includes the sale of drugs. In short: How does Dark Web / Tor Network work You can get an onion browser for iOS on the App Store. How to Access Deep Web without the Tor.
Tor ensures your accessing darknet market privacy and allows you to browse the web without being tracked. The dark web is completely uncensored, which means even if. Female mostly blackish, with fuscous wings.male mostly dark brown exserted portion of abdomen about as in active darknet market urls lunator atrata Both sexes mostly pale. How the Dark Web Operates Tor (The Onion Router) - an open-source toolset designed to enable anonymous communication. Zeronet - decentralized network of peer-. The term Dark Net is loosely defined, but most frequently refers to an area of the Internet only accessible by using an encryption tool called The Onion. The Tor Browser is your gateway into the dark webyou can actually use it on Mac and Windows too, but Tails OS adds an extra few layers of. We believe everyone should be able to explore the internet with privacy. We are the Tor Project, a 501(c)(3) US nonprofit. We advance human rights and. Paper on Dark & Deep Web: Advanced Forensic Analysis of Tor Browser and Implications for Law Enforcement Agencies In this whitepaper.
The main pillars that have built up the dark web are security and privacy. Taking Tor, for instance, it has upgraded from using modified old versions of. TOR allows users to obfuscate browsing activity by scrambling a user's IP address through a secure and distributed network. The TOR project also. Dark web sites aren't indexed as the other surface web sites which we generally uses for our day to day life. TOR (The Onion Router) directs Internet. Darknet markets 2024 reddit Mega dark-net market is a Russian marketplace that new to the Dark Web It is on the Tor platform and similar darknet outlets. Introduction to Tor Tor is a special tool that helps users maintain anonymity when surfing the dark web. The Tor browser leverages onion routing. Find Dread Access Queue tor links on the darkweb, see Dread Access Queue onion Dread is a Reddit-like dark web discussion forum featuring news and. There tor dark web are multiple networks called dark web, all require some software to access the network. You do not need the Tor browser for the dark web.
And the partygoers are the main suspects in the eyes of the police: was it the guy in the devil mask, the guy dressed as Jesus, the bank robber, the construction worker? We monitor larger tor dark web markets (with 100 or more listings) that are in English language. Now there is a solution: in Potatoes Not Prozac Kathleen DesMaisons gives you the tools you need to overcome sugar dependency, with self-tests to determine your sugar sensitivity as well as an easy-to-follow, drug-free program with a customized diet high in protein and complex carbohydrates. If you're familiar with what I said then you'll know that I'm not trying to make any accusations here. All of those networks stay in place because they’re much less visible. The bureau revealed that investigators seized ledgers containing the details of more than 100 people who invested in the scheme. New York Times bestselling author, with 78 published works in seven different series: Dark Series, GhostWalker Series, Leopard Series, Drake Sisters Series, Sea Haven Series, Shadow Series, and Torpedo Ink Series. They rewrote the site's code, they say, to log every user's password, rather than store them as encrypted hashes. Hand inspection of the first 100 results yielded only three true searchable databases; this increased in the second 100 to 7. We have to solve captchas at the login (sometimes even before the login). TranslateMe Telegram Messenger has the same structure as Official Telegram, but the difference in translation.
“They found 31,266 internet URLs with images of child abuse on them, but only 51 (about 0.”
Crypto ransomware uses encryption to maliciously block access to a user’s data. This thesis is restricted to the Claremont Colleges current faculty, students, and staff. This suggests that tor dark web police responses to cryptomarkets result in continued security innovations, thereby making markets more resilient to undercover law enforcement efforts. Financial transactions use Bitcoin, the cryptocurrency that helps assure buyers and sellers anonymity. The tor dark web following 2 days the website was available, but there was no new information. The pre-processing relies on state-of-the-art heuristics 18, 19, 20, 21, 28, including cospending clustering, intelligence-based clustering, behavioural clustering, and entity identification through direct interaction 23. To see the content of the market, place orders, or become one of the sellers you need to register. Wall Street Market (WSM) required its users to trade in virtual currencies, primarily Bitcoin and Monero.








